Cyclic Redundancy Check (CRC): Ensuring Data Integrity in Transmission
In our increasingly digital world, ensuring the integrity and accuracy of data transmission is critical. As data moves across networks, it can be susceptible to errors due to interference, noise, or even hardware malfunctions. One of the most effective methods for detecting these errors is the Cyclic Redundancy Check (CRC). This article will explore what CRC is, how it works, and its significance in ensuring data integrity.
What is Cyclic Redundancy Check (CRC)?
Cyclic Redundancy Check is an error-detecting code used to identify changes or errors in data during transmission or storage. Originally developed in the 1960s, CRC has become a widely adopted technique in networking protocols, file storage systems, and various communication technologies due to its efficiency and reliability.
How CRC Works
The CRC process involves several steps:
- Polynomial Representation:
- Data is treated as a polynomial. Each bit of data is represented as a coefficient in a polynomial of a specific degree. For example, the binary data
1101can be expressed as ( x^3 + x^2 + 1 ).
- Divisor Polynomial:
- A predetermined binary number, known as the generator polynomial, is chosen as the divisor. This polynomial is critical for the CRC algorithm’s effectiveness and determines the error-detecting capabilities of the CRC.
- Binary Division:
- The original data polynomial is divided by the generator polynomial using binary division (similar to long division). The remainder from this division is the CRC checksum. This checksum is appended to the original data before transmission.
- Transmission:
- The data, now accompanied by the CRC checksum, is transmitted over the network.
- Error Detection:
- Upon receiving the data, the receiver performs the same polynomial division using the received data and the same generator polynomial. If the remainder is zero, the data is considered intact. If the remainder is non-zero, an error is detected.
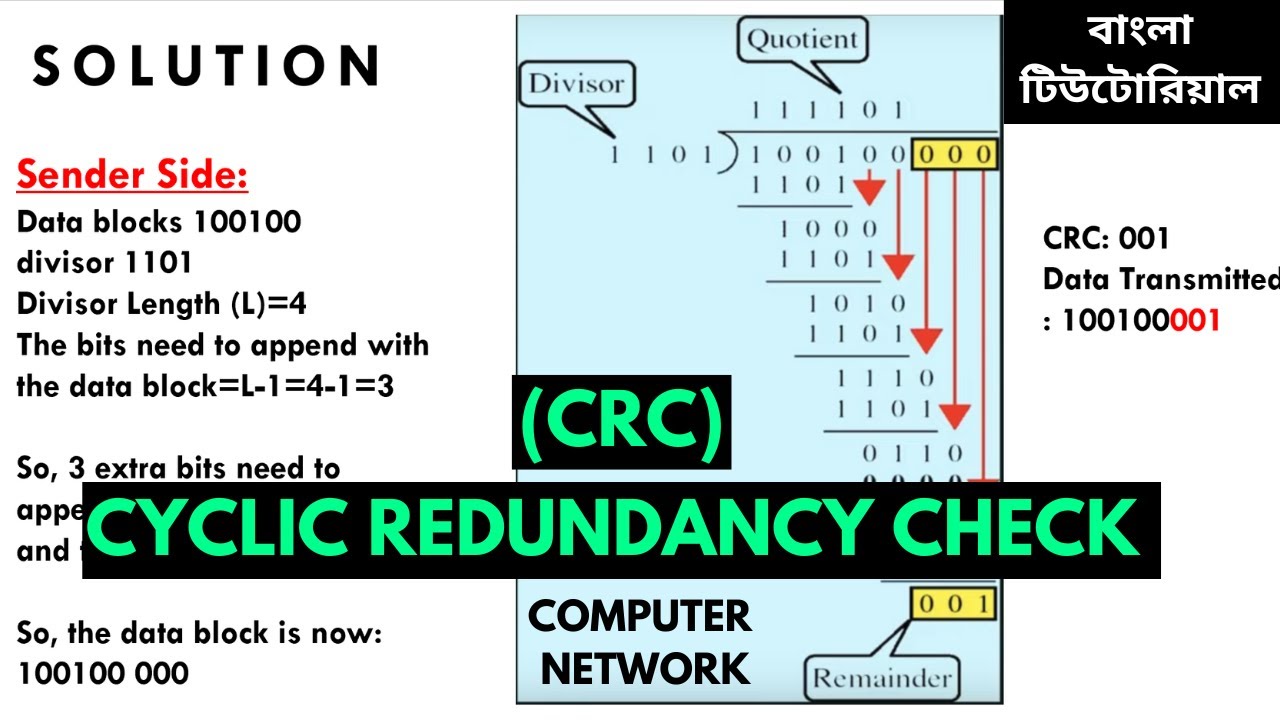
Example of CRC Calculation
Let’s consider a simple example with the following data and a generator polynomial.
- Data:
1101(representing 13 in decimal) - Generator Polynomial:
1011(representing 11 in decimal)
- Binary Division:
1101is divided by1011using binary division.
1011
_________
1101
1011
------
0010 (remainder)- Append Remainder:
- The remainder
0010(in this case) is appended to the original data1101, resulting in the transmitted data11010010.
- Verification:
- The receiver performs the same division on
11010010. If the division yields a remainder of0, the data is valid.
Advantages of CRC
- Error Detection Capability:
- CRC can detect single-bit errors, double-bit errors, and burst errors. Its effectiveness increases with the length of the CRC checksum, making it a robust solution for many applications.
- Efficiency:
- CRC calculations are computationally efficient, allowing for rapid error detection without significantly impacting transmission speed.
- Simplicity:
- The algorithm is simple and can be implemented in hardware or software, making it versatile for various applications.
Applications of CRC
Cyclic Redundancy Check is used in numerous applications, including:
- Networking Protocols: Used in protocols such as Ethernet, USB, and wireless communication standards to ensure data integrity.
- File Storage: Employed in data storage systems to verify the integrity of files and detect corruption.
- Digital Communications: Utilized in modems, satellite communications, and other digital transmission systems to ensure reliable data transfer.
Conclusion
The Cyclic Redundancy Check (CRC) plays a vital role in ensuring data integrity during transmission and storage. By leveraging polynomial division, CRC effectively detects errors that may occur in digital data. Its widespread adoption across various technologies highlights its reliability and efficiency in maintaining the accuracy of information. As data transmission continues to grow, understanding and implementing CRC will remain essential for developers and engineers in safeguarding data integrity.